In this multi-part blog series for Identity and Access Management (IAM), we take a look at IAM capabilities, complexity and challenges organizations face today. We also address why assessing your IAM environment is more critical now than ever before.
Identity and Access Management Series Part 1
Setting the Stage
During previous years of identity management, most identity professionals deployed an on-premise directory domain, which supported common authentication mechanisms such as Kerberos, Negotiate, NTLM, Secure Channel, and Digest. That word “authentication” is one of the four pillars of an Identity. The other three pillars include administration, authorization, and auditing.
Nowadays, when moving to the cloud, we see these authentication mechanisms are less and less useful to us because the federation is the currency of cloud and edge computing today. Federation supports claims-based identity by providing delegated authentication and delegated authorization.
WS-Fed, SAML, and OAuth are such federation sign-in protocols. Think of a federation between two organizations like the watered-down version of an Active Directory trust between two domains. We started with identity terminology, but keep reading as we dive deeper into supporting topics.
Identity and Access Management a Decade Ago
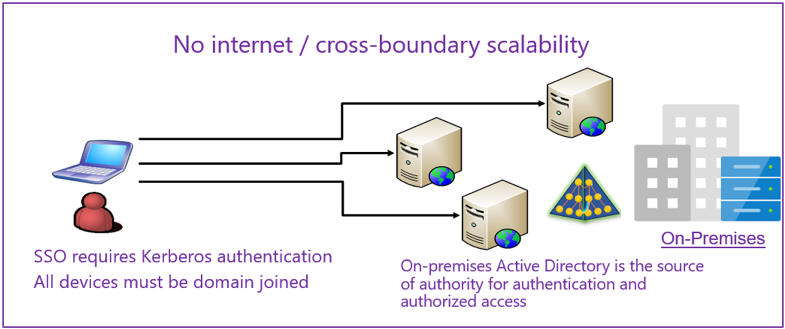
A decade ago, most enterprises had a traditional, centralized IT department delivering capabilities to the business in a highly controlled and locked-down fashion. A typical “on-premise” network perimeter consisted of an Active Directory and Domain joined servers in a company’s data center. Sound familiar?
Active Directory, or some form of another directory, allows users and the computers of an organization to authenticate against resources in the same forest. Or, if there were two forests, via setting up a trust between those forests. On-premise was considered a trusted perimeter. Anything outside the network fell into a hostile category. Authentication in this perimeter then used to be Basic, Digest, Windows Authentication, or forms-based authentication. The below diagram depicts a traditional on-premise IT model.
Identity and Access Management Today
Today, the challenges of securing our environment, particularly from the IAM perspective, is at the top of every organization’s priority list regardless of a company’s size. Identity and Access Management continues to be highly complex, increasing in scope. Digital Transformation initiatives bring about several complexities that did not exist 10 to 15 years ago. Environments are more diverse now. Companies are moving their assets to the cloud.
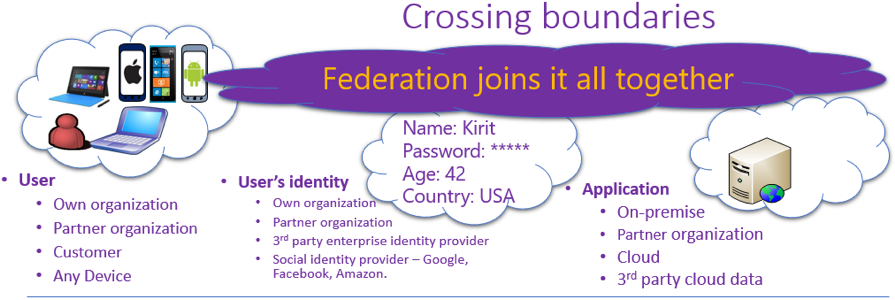
The diagram below shows the evolving identity challenges in the 21st century. Identity solutions cover on-premise and cloud-based capabilities. These solutions create a common user identity for authentication and authorization to all resources, regardless of location. We call this hybrid identity, which we will discuss a little later.
Today’s Identity Challenges
Authentication mechanisms used in the past are no longer effective for today’s cloud and edge focused IoT world. We must leverage alternative identity management approaches to address the increasingly complex landscape. Users with any device (PC, mobiles, and more), anyplace, anytime want to access their application. Challenges in an organization continue to grow as users BYOD (Bring Your Own Devices) and access applications residing anywhere, inside or outside the perimeter, including user’s data. Think about IoT devices in the mix and it makes the above scenario gets even more complex.
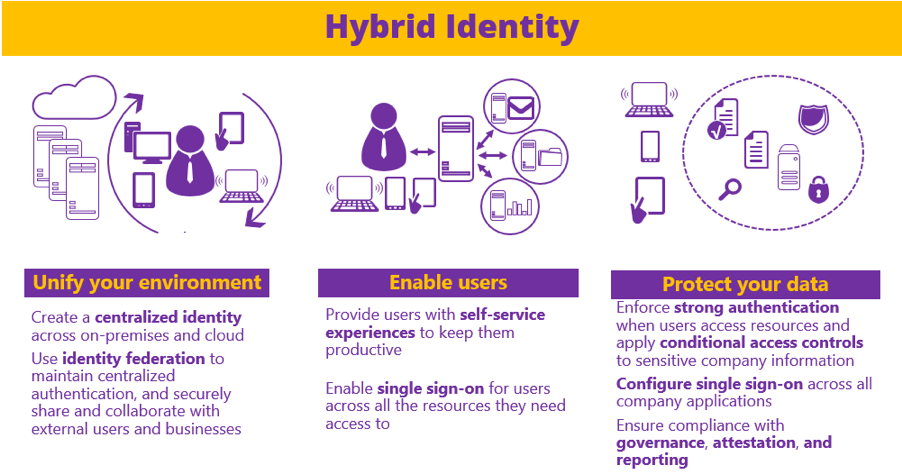
Hybrid Identity
The most common hybrid identity scenarios we hear in our day to day activities are, for example:
- Providing employee access to Office 365
- Integrating with third-party applications and services
- Building new applications or moving existing applications into the cloud
- Providing access to business partners and consumers, which is B2B (Business to Business) and B2C (Business to Consumer), respectively.
There are four primary user identity scenarios across on-premise and cloud.
- Cloud identity provides a solution where all identities, including passwords, live in the cloud. In this scenario, authentication happens in the cloud.
- Identity sync enables customers to bridge their existing identity into the cloud, passwords are in synchronization between on-premise and the cloud, and therefore authentication can occur in either location (depending on what resource is accessed).
- Federated identity allows customers to retain the application’s authentication process to occur on-premise, where the passwords are stored via Active Directory Federation Services (ADFS).
- B2B federated identity allows customers to securely share and collaborate, with each side delegating access to the other resources.
In Conclusion
To make a hybrid identity work, we heavily leverage identity federation. Federation delegates authentication and, therefore, removes the siloed app authentication repositories. It lessens identity management responsibilities for the apps, and it also allows users to leverage an existing identity. Federation also helps in delegating authorization. Applications can change authorization data as appropriate.
Like Hybrid Identity, it is important to add the term “Decentralized Identity,” which we shall cover in our future blog, however, in our next blog, we will introduce Claim Based Authentication (CBA), which provides the foundation of how federation works.
The post Planning IAM’s Success for Enterprises and Consumers in Cloud and Digital Transformation Era appeared first on Centric Consulting.