The threat landscape for website owners is constantly shifting on a regular basis — and it’s becoming increasingly more complex. As attackers continue to develop tools and find new vulnerabilities to massively exploit, our team works diligently around the clock to identify, analyze, and protect hacked websites.
Education is key to protecting yourself from emerging threats. To address this, we are extremely proud to release our 2019 Website Threat Research Report. Sharing these findings with the community helps make the internet a safer place, and educates website owners on the latest trends and threats.
This year, we’ve included a number of new insights to shed light on the most common tactics and techniques we saw within compromised web environments and our remote scanners.
We’ve summarized a few key takeaways from this year’s Website Threat Research Report:
SEO spam was the most common threat found on compromised environments.
62% of websites had an SEO spam infection during our cleanups. Database spam was the most prevailing form of infection. Our remediation team often found database infections without backdoors, which may be related to SQL injections and reflective of our user base.
Almost half of all infected websites contained at least one backdoor.
47% of all infected websites contained one or more backdoors, allowing attackers to maintain access to compromised environments after initial infection.
Core CMS files were found to be vulnerable at the point of infection.
In 2019, over 56% of all CMS applications were out of date at the point of infection.
Primary infection vectors include vulnerable third-party components and software defects.
One of the most common attack vectors seen on websites is related to the improper implementation of the function update_option(). The most common vulnerabilities exploited using this attack vector are stored cross-site scripting attacks and login administration bypasses.
Over 170 million attack attempts were mitigated with the Sucuri Firewall.
The most common types of attacks and malicious behavior blocked by the firewall included bad bots, DDoS attacks, comment spam, and virtual patching for known vulnerabilities.
Cryptomining threat decreased significantly from 2018.
A total of nine new cryptominer domains were blacklisted in 2019, down from 100 in 2018. This trend is likely reflective of the decreased price in cryptocurrencies and the fact that CoinHive, one of the most popular browser-based JavaScript miners on the market, shut down its operations during Q1 2019.
Reinfections are a common issue for previously infected websites.
In 2019, the largest volume of website reinfections occurred for sites infected with SEO spam and generic malware. Our analysts saw 20% of previously infected Magento websites had been reinfected with credit card skimmers, stressing the importance for website owners to follow post-hack protection steps after malware cleanup.
CMS analysis
We measured our monitoring, cleanup, and SiteCheck user bases to identify content management software distribution.
This data is solely a reflection of our customers’ environments, and not of the entire internet at scale.
2019’s data revealed that WordPress was by far the most popular CMS among our user base, accounting for 94.23% of clients in the past year. Joomla (2.49%) followed in at second place, with Drupal (1.28%) taking third.
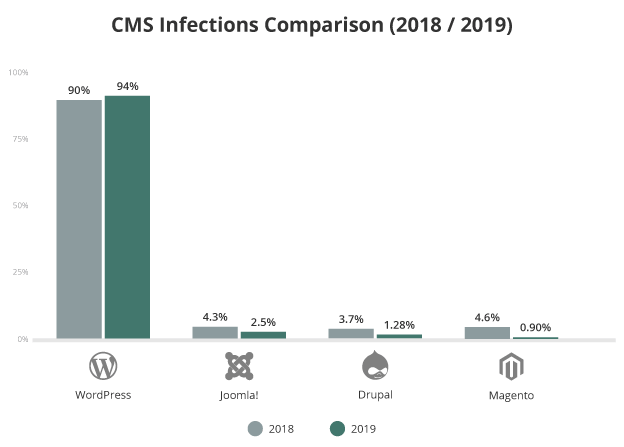
It’s important to note that this data does not imply these platforms are more or less secure than others. This data is purely a reflection of the most common platforms seen in our environment and client base.
Software vulnerabilities
Vulnerable software is one of the leading causes for website infections — and the number of readily available exploits available to hackers is vast. Automated scripts make it extremely easy to scan websites for known vulnerabilities.
Our team saw more high-severity vulnerabilities in 2019, partly due to the rise of attacks targeting the improper use of the WordPress update_option() function.
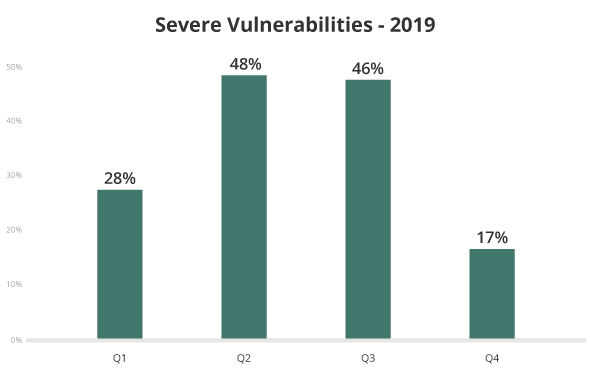
To mitigate the risk of automated scripts locating and infecting a website by exploiting a known vulnerability, it’s imperative that website owners keep all website software up to date with the latest security patches.
Outdated CMS analysis
Our latest report also assesses the number of outdated CMS applications at the point of infection.
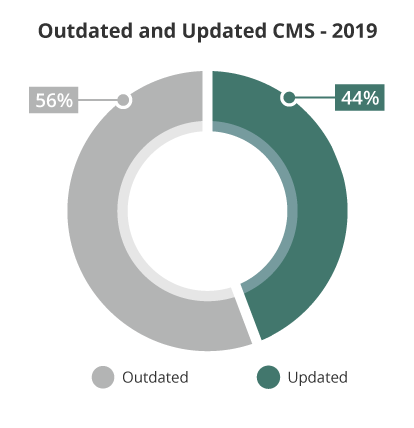
In 2019, we saw that 56% of all CMS applications were out of date at the point of infection. This number was virtually unchanged from our 2018 hacked website trend analysis.
In 2019, 56% of websites were outdated at the point of infection.
Vulnerable components & exploits
During 2019, we continued to see long-lasting malware campaigns targeting deprecated, vulnerable versions of plugins and components.
A large percentage of the plugins found on compromised websites were unpatched, exposing users to the risk of known vulnerabilities being exploited. Our analysis revealed that 44% of all vulnerable websites had more than one vulnerable software components present in the environment — 10% of which had at least four vulnerable components.
Always keep your plugins, themes, and other third-party components updated with the latest security patches to protect against known vulnerabilities.
Website reinfections
Sites that had been infected with spam and malware experienced the largest volume of reinfections when compared to other families.
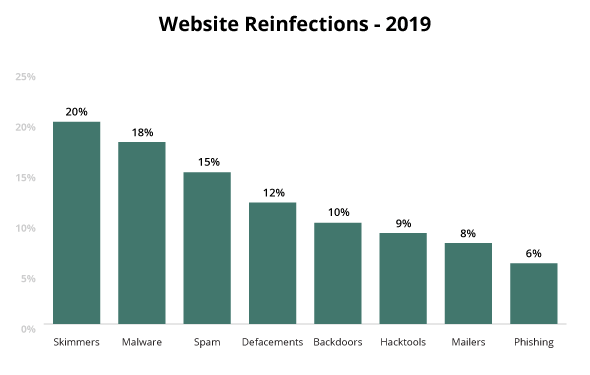
More than half of spam reinfections were related to SQL injections (53%) in 2019. We also saw that Magento sites were reinfected with credit card skimmers 20% of the time.
20% of infected Magento websites were reinfected with credit card skimmers in 2019.
Firewall blocks & attack vectors
A total of 170,827,313 attack attempts were blocked by our firewall in 2019, a 52% increase from 2018.
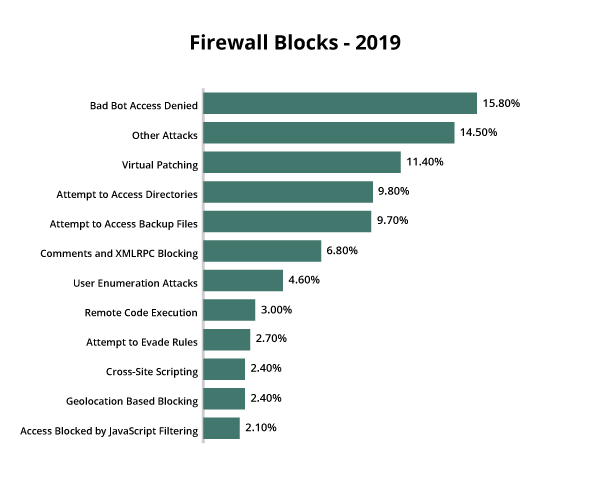
Bad bots
The largest number of firewall attack attempts were made under the Bad Bot Access Denied category, which is triggered when we block malicious bots from accessing a client’s website.
15.80% of all firewall block attempts were from malicious bots in 2019.
Other attacks
The second largest number of blocked attack attempts fell under the “Other” category, which includes generic rules for geoblocking, SQL injections, remote file inclusions, spam attempts, and remote code injections.
Virtual patching
Whenever our team finds or analyzes a vulnerability, we create a firewall rule to filter, detect, and mitigate an exploit. By leveraging our virtual patching services, our clients are able to prevent a hacker from exploiting a software vulnerability on their website.
In 2019, 11.40% of blocked attack attempts were targeting known vulnerabilities.
[ Read More About Attack Vectors from the 2019 Report ]
Top detected malware
Our team aggregated and analyzed signatures used during malware cleanup and incident response.
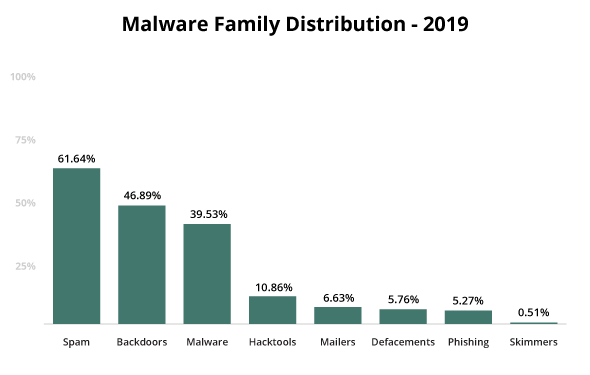
We found that spam continues to be the most common infection found on client sites.
During 2019, 62% of client sites contained SEO spam. Infections typically occur via PHP, database injections, or .htaccess redirects.
Our data showed an average of 12 different types of injected spam on a single website. The most common type of SEO spam malware was found in the database and responsible for infecting websites with unwanted content.
Common spam content
Our team analyzed SEO spam keywords from SiteCheck and discovered that 59% of spam content was related to pharmaceutical industries, with viagra (31%) and cialis (17%) being the most common keywords in this category.
Top spam themes
- Viagra
- Cialis
- Sport jerseys
- Pharmacies/no prescriptions
- Replica watches
- Porn
- Turkish escort spam
- Essay spam
Another 34% of spam detections were related to replica merchandise like those found for fake NFL/NHL sport team jerseys.
59% of spam was related to pharmaceuticals and male enhancement keywords in 2019.
Website backdoors
Another extremely common threat found within compromised site environments were backdoors. In fact, 47% of all infected websites were found to contain at least one backdoor in 2019.
There are a number of steps website owners can take to prevent website backdoors:
- Employ file integrity monitoring tools to identify indicators of compromise.
- Create and maintain strong, unique passwords on all accounts.
- Use a firewall to filter malicious activity and block access to backdoors.
- Keep all software patched with the latest security updates to mitigate risk.
Conclusion
This is only a brief summary of some of the highlights and findings from our 2019 threat report, which expands on this data and includes further analysis of topics like blacklisted resources, malware families, attack vectors, and cleanup signatures.
The threat landscape hasn’t changed much since our last report. Massive, ongoing malware campaigns continue to evolve and there has been a shift in attack vectors, with attackers targeting and exploiting vulnerabilities in popular third-party components.
SEO spam infections continued to be the most common type of malware found within compromised environments, with nearly half of compromised websites containing backdoors that allow attackers to maintain access after the initial infection.
Looking ahead for the new year, our predictions are not very surprising; the most popular attacks against websites will continue to be the most profitable ones — including SEO spam and payment card data theft.
The post Hacked Website Threat Report – 2019 appeared first on GoDaddy Blog.


















